- Log in to Round cube.
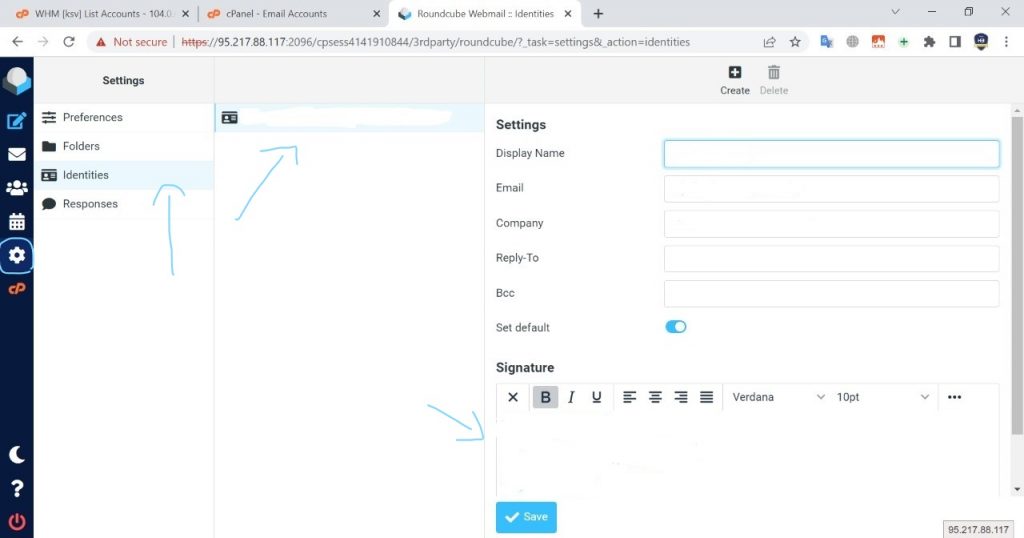
- In the side menu bar, click Settings.
- Click Identities.
- Click on your signature and edit your signature.
- Click Save.


In order to register .com.au domain names, you’ll need a check on your eligibility. To be eligible, registrants need to fulfill one of the following criteria, being either:
As well as registering .com.au, the above also applies to acquire. net.au names. Eligibility for other .au website addresses can be viewed in our domain name registration guide.
A valid application with accurate details must be submitted and approved before .com.au domain name is considered to be fully licensed, but this is a very rapid process if you use our service.
This submission procedure fully occurs online as part of your name registration process and we will only contact you if further details are required.
Your online registration application will be assessed to determine both that the information provided is valid and that it meets the allocation criteria. While this process may seem onerous, it serves to protect the integrity of the .com.au space and is one of the reasons why. com.au domain names remain one of the most trusted extensions; both locally and overseas. The eligibility criteria and process help to protect registrants as well.
If you’re unsure of your eligibility to register .com.au domains, please feel free to contact our office for clarification or check if you’re eligible.
We also recommend you refer to our domain name registration tips guide before you register .com.au website addresses for further information and handy advice about domain name selection and choosing the right address for your purposes.
| Basic | Business | Pro | Premium | Ultra |
|---|---|---|---|---|
| 699/mo | 1399/mo | 2499/mo | 4699/mo | 8599/mo |
| 1 vCPU | 2 vCPU | 2 vCPU | 4 vCPU | 8 vCPU |
| 2 GB RAM | 4 GB RAM | 8 GB RAM | 16 GB RAM | 32 GB RAM |
| 20 GB Disk space | 40 GB Disk space | 80 GB Disk space | 160 GB Disk space | 240 GB Disk space |
| 20 TB Traffic | 20 TB Traffic | 20 TB Traffic | 20 TB Traffic | 20 TB Traffic |
The active scanning of files can help prevent exploitation of an account by malware by deleting or moving suspicious files to quarantine before they become active. It can also prevent the uploading of PHP and perl shell scripts, commonly used to launch more malicious attacks and for sending spam.
cxs also allows you to perform on-demand scanning of files, directories and user accounts for suspected exploits, viruses and suspicious resources (files, directories, symlinks, sockets). You can run scans of existing user data to see if exploits have been uploaded in the past or via methods not covered by the active scanning. It has been tuned for performance and scalability.
Included with the cxs Command Line Interface (CLI) is a web-based User Interface (UI) to help:
few client using airtel connection have facing issue with yandex email usage from web and outlook.
Here is temporory solutions
Out service provider operates two own data centers for dedicated servers and colocation services. The ultra-modern “green data center“ in Munich was constructed and builtin 2009 and has enough room for 4,000 servers. The second data center in Nuremberg has been launched in 2014, and it offers space for another 10,000 dedicated servers. On both locations the office rooms are in the same building, only one level above the data floor.
Both data centers are state of the art, especially when it comes to operational safety and energy efficiency. DC invests large amounts in the maintenance and optimization of the entire data center infrastructure every year. This allows us to offer customers a stable and – thanks to low operational costs – economical hosting platform.
Both data centers are located in different cities being several hundred kilometers apart from each other, and both are powered by different electricity suppliers (SWM and N-Ergie). Thus, your servers can be distributed to different locations without additional costs for you. Due to this geographical redundancy your services will stay online even if it comes to the highly unlikely case that one data center will be damaged by fire, water, or any other imaginable disaster.
In 2017 the data center in Nuremberg has been awarded by an expert jury of independent data center experts from Germany with the German Data Center Award 2017, the Deutsche Rechenzentrumspreis. In 2018 the Data center in Munich has also been awarded with the German Data Center Award, the Deutsche Rechenzentrumspreis. So both data centers are award-winning.
Facts about the data
Location: Munich – Germany
Nuremberg – Germany
Data center area: 300 m² (Munich)
1750 m² (Nuremberg)
Air conditioning: Multiple chillers (n+1)
Groundwater cooling system
Several climate cabinets (n+1)
100 % redundant
Free cooling
Energy-efficient
Remote-controlled
Expandable
Internet access: Carrier-neutral
Numerous different fiber carriers using at least two different fiber directions into the building
The data centers are currently connected to the Internet with 130 Gbit/s:
Energy supply: Inhouse transformer-station
Multiple UPS with batteries (n+1)
Emergency backup generator with powerful diesel generator
Security: Access only via ID card
Alarm system
Security service on duty
More than 50 observation cameras and video recording
Several live-webcams
Smoke detector / automatic fire alarm
Smoke exhaust installation
Water detector
Environment: Hundreds of power outlets per room, mounted directly into the double floor
Every single power outlet electrically interlocked at 16 A
Cable bushings mounted into the double floor next to the power outlets
Completely locked double floor
AC ventilation grills, individually adjustable, mounted into the double floor
Cool water canalization only beneath the double floor
Gullies for the case of a pipe leakage
19”-Racks individually lockable
Cages, entire colocation rooms for single customers and individual modifications/equipment available
Satellite feed (Astra 19.2°E and Eutelsat Hot Bird 13.0°E)
Service: Personnel on site 365 days a year, also on holidays and weekends. Priority and emergeny support available
recent phishing attach
many of our clients are complaining regarding emails as bellow we suggest remedies bellow
but you should take the following corrective steps
Sample Mail Copy
Hello!
My nickname in darknet is xxxxx.
I hacked this mailbox more than six months ago,
through it I infected your operating system with a virus (trojan) created by me and have been monitoring you for a long time.
the error you will see above mail
Many people marked similar messages as phishing scams, so this might contain unsafe content. Avoid clicking links, downloading attachments, or replying with personal information.
open .htaccess and apply this code
this Setting “expires” tells browsers downloading these files that they don’t need to request it again for this specific length of time. In other words, use the cache instead if you have it. This can reduce stress on the server for you, and speed up page load time for visitors.
# BEGIN EXPIRES
<IfModule mod_expires.c>
ExpiresActive On
ExpiresDefault “access plus 10 days”
ExpiresByType text/css “access plus 1 week”
ExpiresByType text/plain “access plus 1 month”
ExpiresByType image/gif “access plus 1 month”
ExpiresByType image/png “access plus 1 month”
ExpiresByType image/jpeg “access plus 1 month”
ExpiresByType application/x-javascript “access plus 1 month”
ExpiresByType application/javascript “access plus 1 week”
ExpiresByType application/x-icon “access plus 1 year”
</IfModule>
# END EXPIRES